As systems become increasingly decoupled, APIs are both the connective tissue and a growing attack surface. Designing secure API gateways is critical for tech leaders seeking to maintain performance without sacrificing control.
Here’s a handy flowchart so you can visualize the process first:
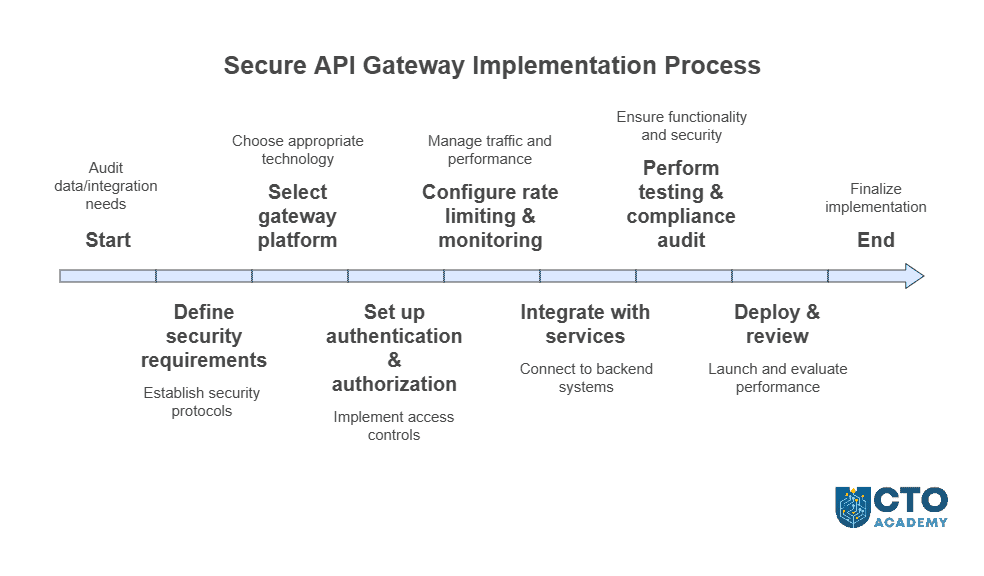
1. Audit Integration Needs
- Start by inventorying APIs by function, sensitivity, and exposure (internal, partner, public).
- Determine SLA and performance expectations for each class.
2. Define Security Requirements
Set your baseline: TLS enforcement, OAuth2 or JWT for authentication, and granular RBAC for authorization. Align these controls with your data classification.
3. Select Gateway Architecture
- Choose between cloud-native (e.g., AWS API Gateway), open-source (e.g., Kong, Tyk), or self-hosted platforms.
- Prioritize extensibility and vendor lock-in avoidance.
4. Implement Access Controls
- Configure API keys, usage quotas, IP whitelisting, and client-specific rate limiting.
- Enable multi-tenant support if needed for partner APIs.
5. Monitor, Log, and Alert
Integrate observability tools (e.g., Datadog, Prometheus) for metrics and logging.
TIP: Make sure to implement automated alerts for unusual behavior or security violations.
6. Connect to Services Securely
- Ensure least privilege access when routing requests to backend services.
- Use service meshes or encrypted tunnels to maintain confidentiality.
7. Conduct Security Reviews and Testing
- Apply static analysis, fuzz testing, and penetration testing regularly.
- Address findings before production releases.
8. Iterate and Automate
- Integrate gateway configurations into your CI/CD pipelines.
- Track policy changes and security incidents in a shared dashboard.
With a secure API gateway design, technology leaders can enable innovation without exposing the organization to unnecessary risk. Remember, the gateway is not just a router — it’s a governance guardrail.

